Alerting With Audit Logs
If you have a logging aggregator in place, you can leverage Audit Logs and the data they provide to get notifications or alerts for certain Audit Events.
This isn’t a detailed tutorial on logging aggregators or how to use Datadog. The goal of this document is to show how the data provided by Audit Events can help you setup alerts for events of interest.
Alerting and logging aggregators
The following section uses Datadog to exemplify using Audit Logs to receive alerts for certain actions. There are many Logging Aggregator tools that can help you with this in similar ways.
Setting up logs collection
Assume that we have a pre-existing Audit Logs configuration in Connect:
/etc/rstudio-connect/rstudio-connect.gcfg
[Logging]
AuditLog = "/var/log/connect-audit.log"
AuditLogFormat = "JSON"With Datadog logging enabled, the following setting configures the Datadog agent to collect audit logging entries:
/etc/datadog-agent/conf.d/rstudio-connect.d/conf.yaml
logs:
- type: file
path: /var/log/connect-audit.log
service: rstudio-connect
source: rstudio-connectIt is very likely that you will need to adjust permissions so that your logging aggregator can tail the audit logs file. E.g.,: sudo chmod 0644 /var/log/connect-audit.log
Setting up a monitor
To setup a monitor in Datadog to trigger alerts, first create a New monitor. Then click the Logs option.
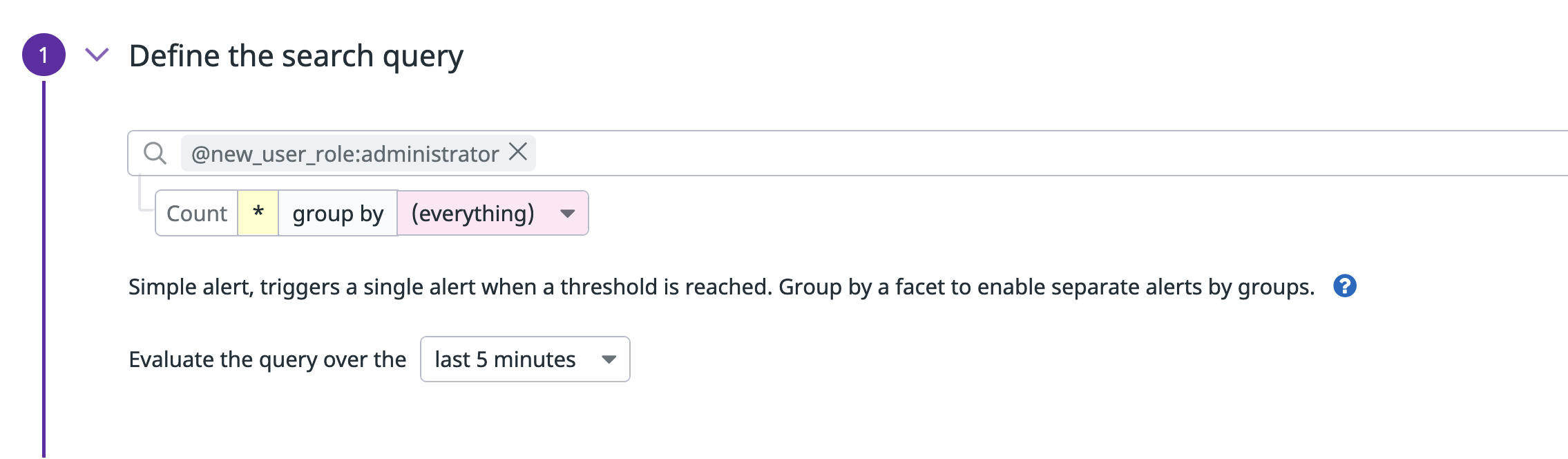
Define the search query
You can track when user roles change. For example, when a user is granted the Administrator role. The edit_user event provides a data field named new_user_role which fires when there are updates to a user role and indicates the new role assigned. You can make use of this information by setting @new_user_role:administrator as the search query. The new monitor considers any new audit log entries that contain the "new_user_role": "administrator" field.
In Datadog, the @ syntax indicates that you want to access an attribute from the log record.
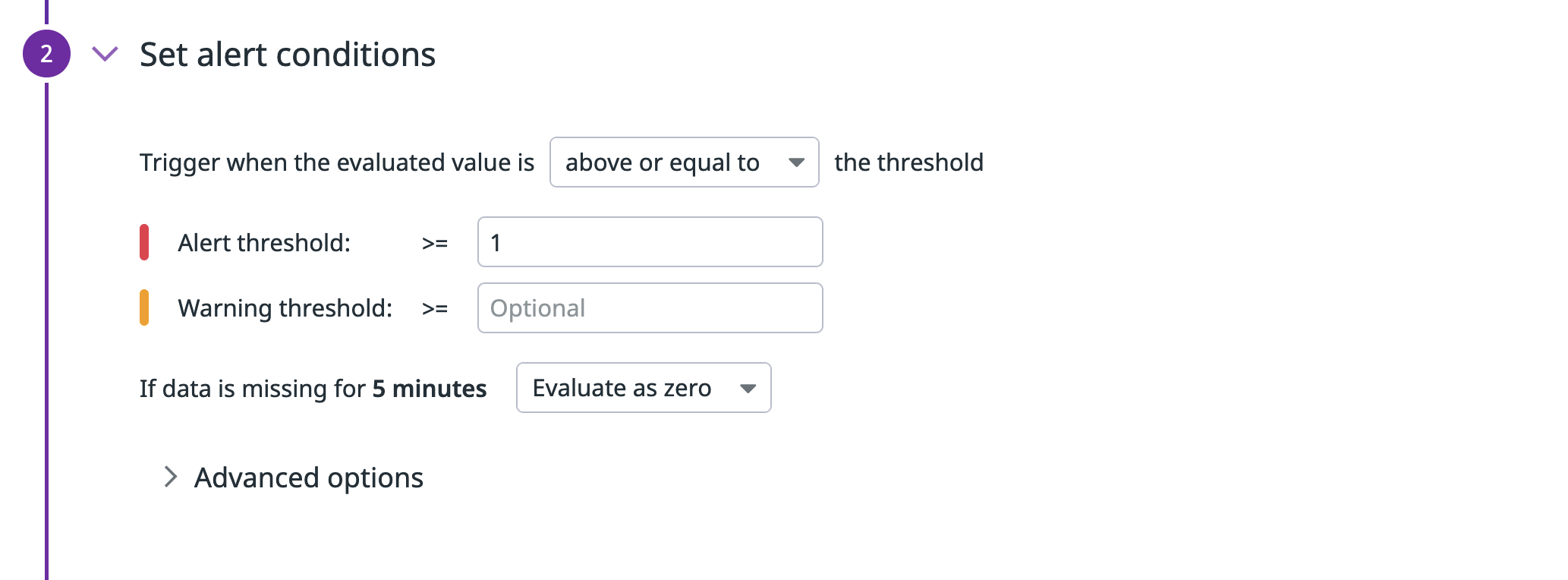
Set alert conditions
For this alert, you can specify it to trigger every time a user is granted the administrator role. That means an "Alert threshold" of "above or equal to" "1".
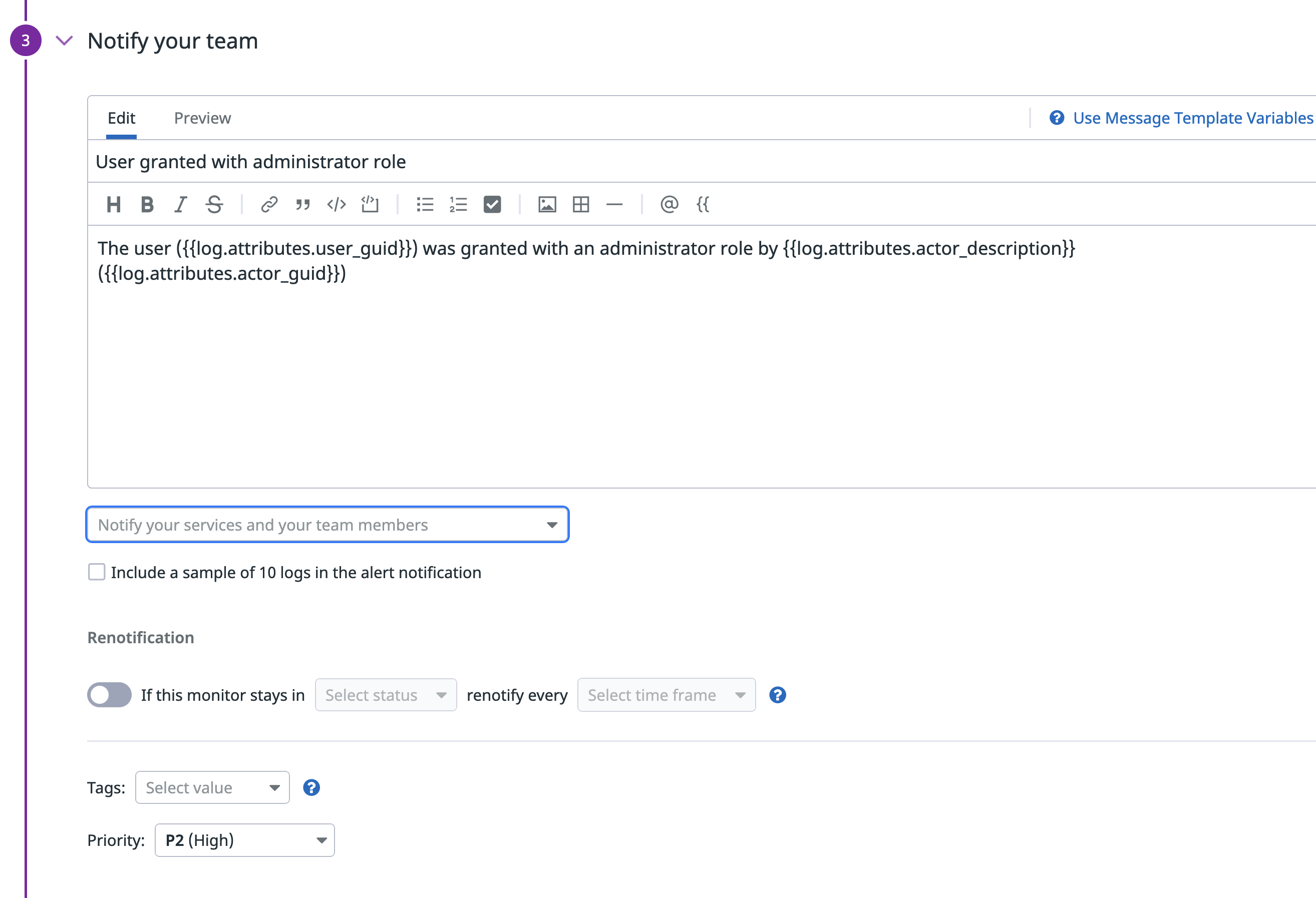
Craft the alert message
The edit_user event provides many useful data fields. This example makes use of user_guid, actor_description and actor_guid to craft a simple message that includes the unique identifiers for both the new administrator user and the user who made the change.
To use the audit log record data in the Datadog message template, we have to prefix the log field with log.attributes.
For the message subject, configure User granted with administrator role, and for the message body use the following template and set the log.attributes of our interest.
Message Body
{% raw %}
The user ({{ "{{log.attributes.user_guid}}" }}) was granted an administrator role by {{ "{{log.attributes.actor_description}}" }}
({{ "{{log.attributes.actor_guid}}" }})
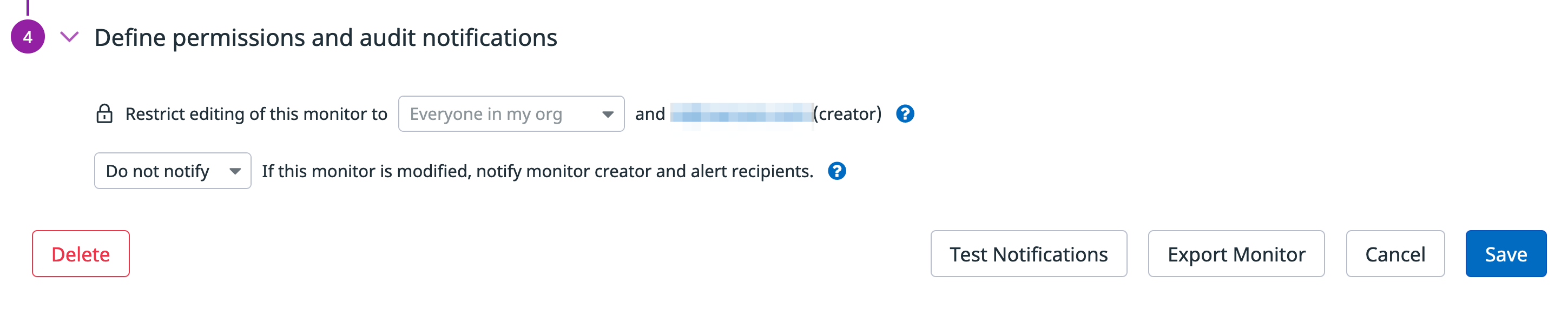
{% endraw %}Define monitor permissions
To finish creating the monitor, define who can modify it and who to notify when a modification happens. For this example, leave the defaults and click Save.
The new monitor in action
With Datadog collecting your Audit Logs and with the new monitor ready and saved, the next time a user is updated with an administrator role, an email alert is sent and the monitor in Datadog registers the event.
The New Monitor Dashboard 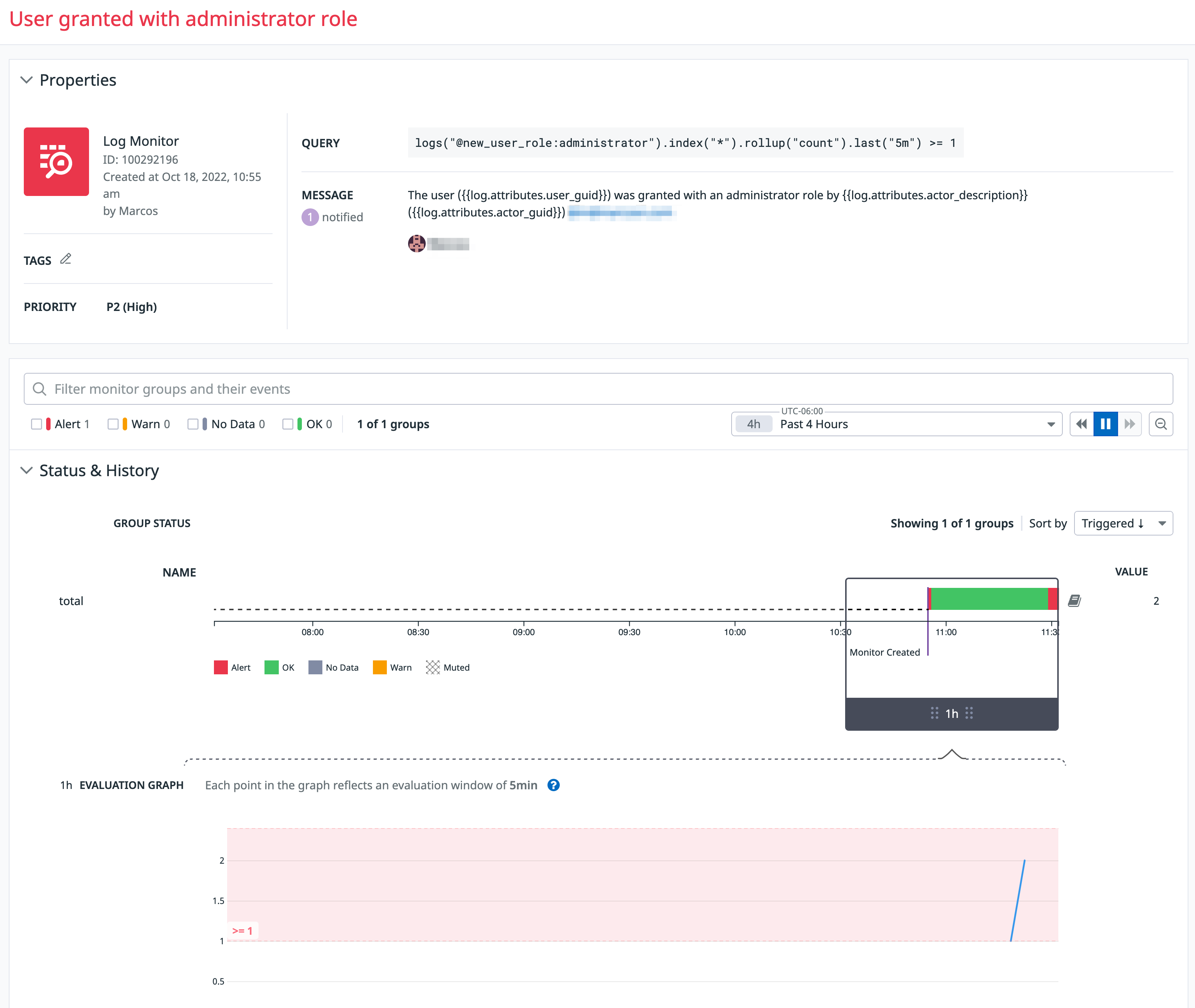
Email Alert 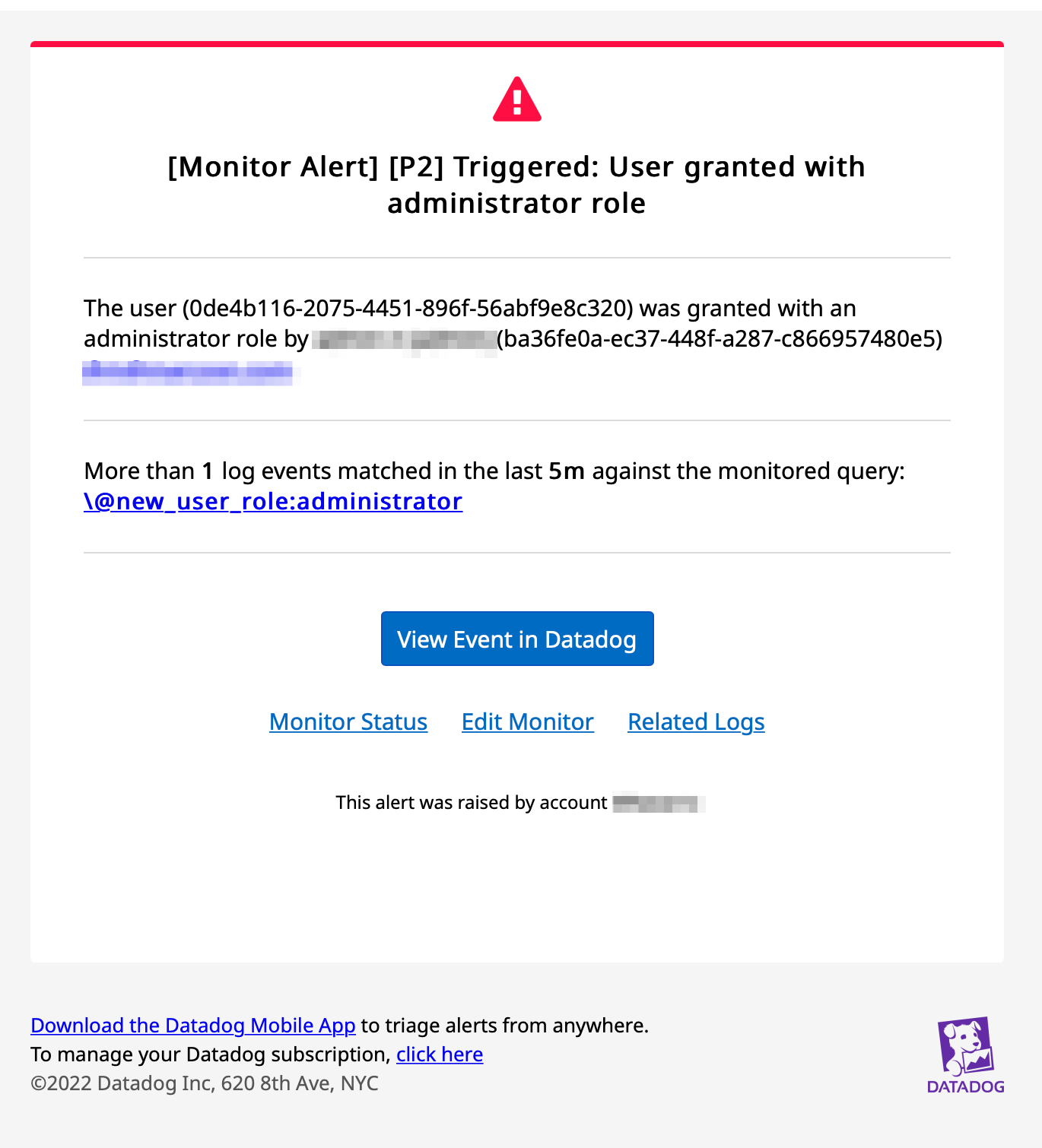
Recommended events to monitor
User activity
User role elevation
Monitor user role elevation to administrator to detect unauthorized access, identify insider threats, ensure compliance, and maintain the principle of least privilege.
Query: @new_user_role:administrator
Failed login attempts
Monitor and alert on repeated failed login attempts for early detection of potential security threats, such as unauthorized access attempts or brute-force attacks.
Query: @action:user_login_failure
Admin account monitoring
Content access privilege escalation
Monitor when an administrator escalates their own privilege on content that is not owned by them. This helps ensure accountability, adherence to established procedures, and compliance with the principle of least privilege. Preventing unauthorized or potentially risky actions helps avoid compromising the integrity of systems and data.
Query: @actor_role:administrator @action:assign_user_app_role owner
API key creation
Monitor creation of administrator API keys to detect potential unauthorized access.
Query: @action:add_api_key @actor_role:administrator
All activity
Monitor all admin activity to enable timely detection of suspicious behavior, help enforce compliance with policies and regulations, ensure accountability, and facilitate rapid response to potential security incidents.
Query: @actor_role:administrator
Content sharing
Access to sensitive content
Monitor all activity on sensitive content using the content GUID.
(Replace the uuid in the query below with the appropriate content GUID)
Query: @content_guid:1a2b3c45d-6f70-8bcc-9b87-c654a3ff2045