Custom
Configuring a Custom OAuth integration in Posit Connect involves two main steps, each performed by different administrators.
- Step 1: An OAuth provider administrator registers an OAuth application.
- Step 2: A Posit Connect administrator creates an OAuth integration within Connect.
This guide walks through both steps of this process, providing the necessary information for each administrator role.
Step 1: OAuth provider administrator
Create application in OAuth Provider
Register application
The administrator of the OAuth provider must register Connect as an application before an OAuth integration can be configured.
Viewer Integration
The administrator adds a redirect_uri for the OAuth application as seen in the screenshot below. The OAuth provider sends the user credentials to the redirect_uri at the end of the OAuth handshake, allowing Posit Connect to obtain a temporary access token and refresh token.
The OAuth application is configured with the following redirect URL (sometimes referred to as a callback URL): https://connect.example.org/__oauth__/integrations/callback. Replace connect.example.org with the address of the Connect server.
For OAuth application administrators who prefer to use the same OAuth application for both Posit Connect and Posit Workbench, simply register the Workbench redirect URL (https://workbench.example.org/oauth_redirect_callback) in addition to the Connect redirect URL.
Service Account Integration
Service account integrations do not direct the user through a login flow, so a redirect_uri is not required.
Transfer information to Connect Administrator
The administrator of the OAuth provider shares the following information with the Posit Connect administrator:
| Field | Description |
|---|---|
client_id |
Unique identifier for the OAuth application. |
client_secret |
Secret identifier for the OAuth application. Not required for Public Viewer integrations. |
authorization_uri |
The URI for the authorization endpoint. Can also be obtained from the Authorization Server Metadata Endpoint. |
token_uri |
The URI for the token endpoint. Can also be obtained from the Authorization Server Metadata Endpoint. |
token_endpoint_auth_method |
Determines how parameters are passed to the OAuth application. This is a property of the OAuth application itself. |
scopes |
The permissions requested by Connect. |
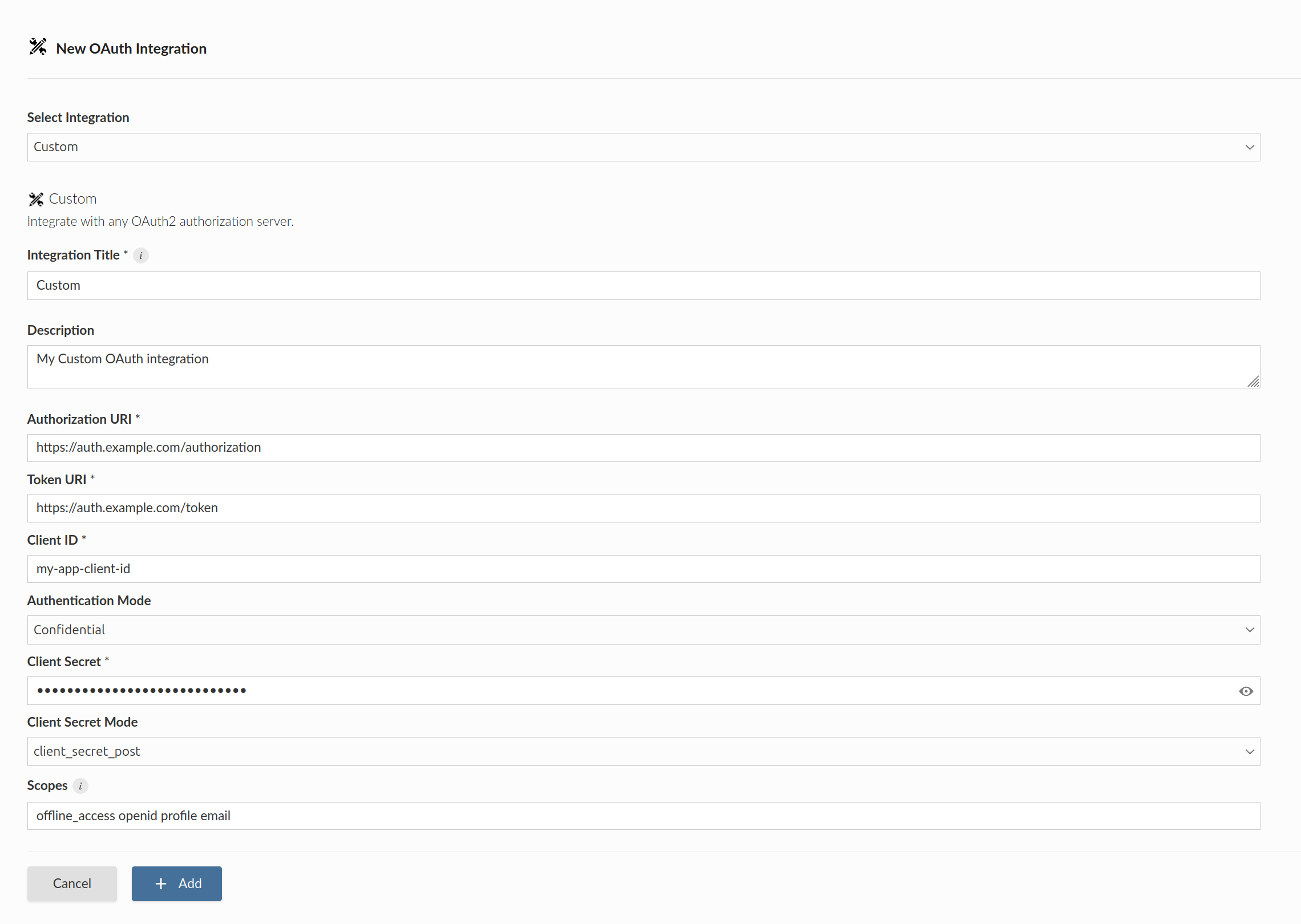
Step 2: Posit Connect administrator
Create OAuth integration in Posit Connect
Using the information from the OAuth provider administrator, the Posit Connect administrator creates an integration through the dashboard’s System > Integrations settings. Once the OAuth integration has been created in Connect, it is available for use by all publishers.
Ensure the proper authentication type is selected for the type of credentials that will be retrieved from the OAuth provider. See the documentation on supported authentication types for more information.
Alternatively, the example below shows how to create a Confidential Custom OAuth integration using curl and the Connect Server API. Replace connect.example.org with the address of the Connect server.
Terminal
curl -H "Authorization: Key ${CONNECT_API_KEY}" \
-XPOST https://connect.example.org/__api__/v1/oauth/integrations \
--data '{
"template": "custom",
"name": "Custom OAuth integration",
"description": "A helpful description for publishers to use when choosing an OAuth integration for their content.",
"config": {
"auth_type": "Viewer",
"auth_mode": "Confidential",
"client_id": "<client-id>",
"client_secret": "<client-secret>",
"authorization_uri": "<authorization-endpoint>",
"token_uri": "<token-endpoint>",
"scopes": "offline_access openid profile email"
}
}'
# 200 OK
# {"guid": "<oauth-integration-guid>", ... }OAuth integrations in Connect use the PKCE (Proof Key for Code Exchange) extension for the authorization code flow by default. PKCE is required in the upcoming OAuth 2.1 specification, and is recommended in all cases to protect against authorization code injection attacks. If necessary, PKCE can be disabled by creating a Custom integration with "use_pkce": false in the config map, but this is not recommended.