Snowflake
Configuring a Snowflake OAuth integration in Posit Connect allows content to access Snowflake data securely. Connect supports two authentication types when configuring an integration, depending on your use case:
- Viewer integration: Used when applications should run on behalf of the logged-in user.
- Service account integration: Used when applications run automatically (e.g., scheduled reports) without a user present, using a service account.
Viewer integration
This flow involves two main steps, each performed by different administrators.
- Step 1: A Snowflake administrator registers an OAuth application in Snowflake.
- Step 2: A Posit Connect administrator creates an OAuth integration within Connect.
Step 1: Snowflake administrator
The Snowflake administrator registers an OAuth Application in Snowflake.
The Snowflake administrator adds a redirect_uri for the OAuth application. This redirect is where Snowflake sends the user’s OAuth credentials at the end of the OAuth handshake. This allows Posit Connect to obtain a temporary access token and refresh token from Snowflake.
Connect currently only supports integrations which target Confidential Snowflake OAuth applications. Confidential applications require clients to authenticate with a client secret.
The following example uses Snowflake SQL’s CREATE SECURITY INTEGRATION command to create a new OAuth application. Replace connect.example.org with the address of the Connect server.
CREATE SECURITY INTEGRATION POSIT_CONNECT
TYPE = OAUTH
ENABLED = TRUE
OAUTH_CLIENT = CUSTOM
OAUTH_CLIENT_TYPE = 'CONFIDENTIAL'
OAUTH_REDIRECT_URI = 'https://connect.example.org/__oauth__/integrations/callback'
OAUTH_ALLOW_NON_TLS_REDIRECT_URI = FALSE
OAUTH_ISSUE_REFRESH_TOKENS = TRUETo obtain the client ID and secret, use the following command:
SELECT SYSTEM$SHOW_OAUTH_CLIENT_SECRETS('POSIT_CONNECT');Transfer information to Connect administrator
The Snowflake administrator shares the following information with the Posit Connect administrator:
| Field | Description |
|---|---|
account_url |
URL of your Snowflake account. |
client_id |
The client ID obtained by querying the security integration. |
client_secret |
The client secret obtained by querying the security integration. |
scopes |
The permissions requested by Connect. See the Snowflake OAuth documentation for information on supported scopes. |
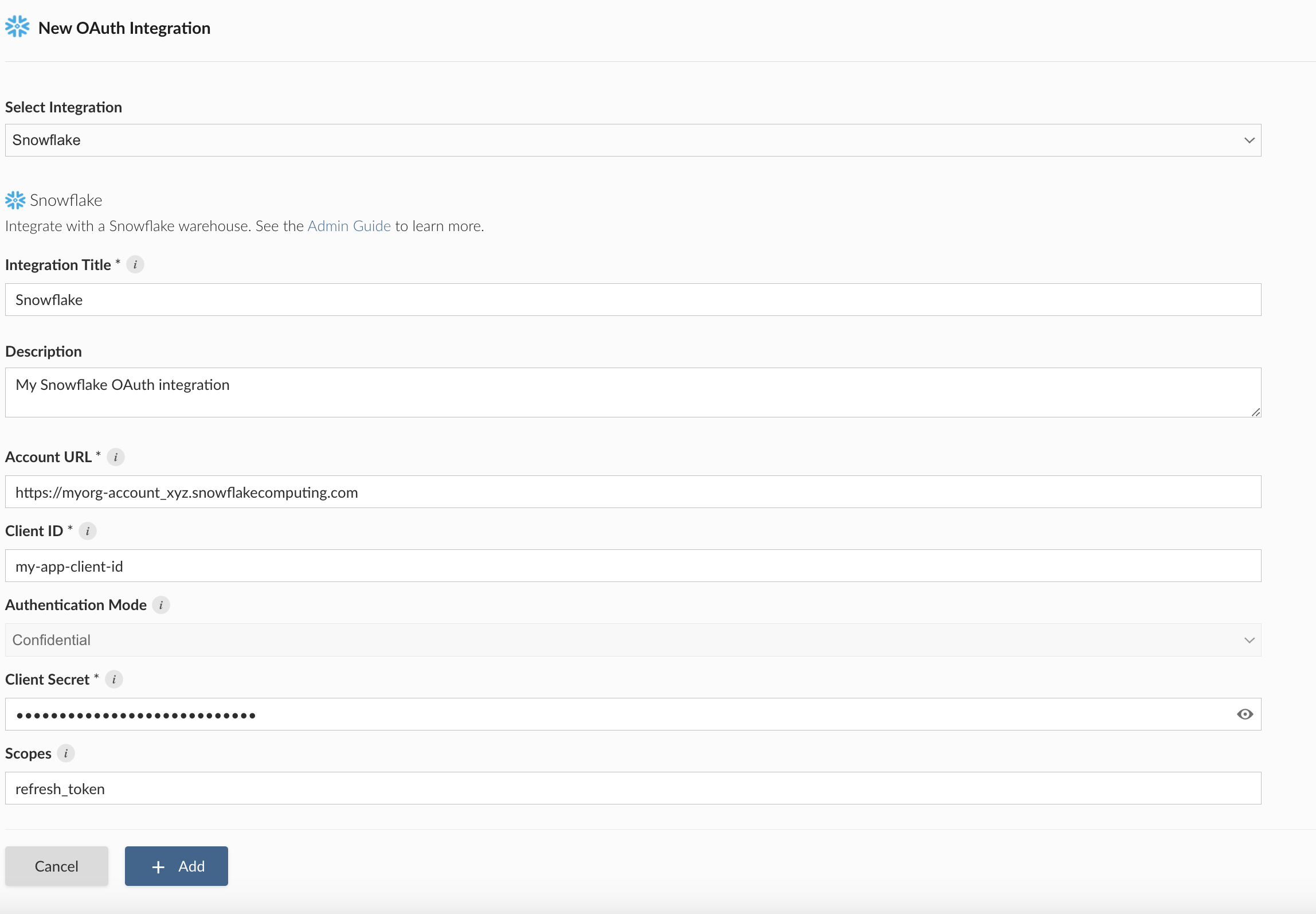
Step 2: Posit Connect administrator
Using the information from the Snowflake administrator, the Posit Connect administrator creates an integration through the dashboard’s System > Integrations settings. Once the OAuth integration has been created in Connect, it is available for use by all publishers.
Alternatively, the example below shows how to create a Snowflake OAuth integration using curl and the Connect Server API.
Replace:
connect.example.orgwith the address of the Connect server.https://myorg-account_xyz.snowflakecomputing.comwith the Snowflake account URL.
Terminal
curl -H "Authorization: Key ${CONNECT_API_KEY}" \
-XPOST https://connect.example.org/__api__/v1/oauth/integrations \
--data '{
"template": "snowflake",
"name": "Snowflake OAuth integration",
"description": "A helpful description for publishers to use when choosing an OAuth integration for their content.",
"config": {
"account_url": "https://myorg-account_xyz.snowflakecomputing.com",
"client_id": "<snowflake-client-id>",
"client_secret": "<snowflake-client-secret>"
}
}'
# 200 OK
# {"guid": "<oauth-integration-guid>", ... }Service account integration
Snowflake supports service account OAuth integrations through OAuth federation with external identity providers using the client credentials grant flow.
For automated workflows (backend services, machine-to-machine communication, or scheduled jobs) where no interactive user is present, you should use this type of OAuth integration.
In this architecture, Snowflake acts as the Resource Server, but it relies on an external Authorization Server (such as Microsoft Entra ID / Azure AD) to issue tokens. Connect authenticates with the external provider, obtains a token, and passes it to Snowflake.
This requires configuring External OAuth in Snowflake.
Configuration workflow
Configure the identity provider (e.g., Microsoft Entra ID)
You must register two applications in your identity provider:
- OAuth Resource (Snowflake): Represents the Snowflake instance. You will define scopes/App Roles here (e.g.,
session:role:ANALYST). - OAuth Client (Connect): Represents Posit Connect. This application requires a Client ID and Secret and must be granted API permissions to the Snowflake Resource created above.
For a comprehensive guide on configuring these resources in Microsoft Entra ID, refer to the Snowflake community article: OAuth 2.0 Client Credentials Grant to Snowflake with Microsoft Entra ID.
Configure external security integration
The Snowflake administrator must create a security integration of type EXTERNAL_OAUTH. This tells Snowflake to trust tokens issued by your Identity Provider.
CREATE SECURITY INTEGRATION EXTERNAL_OAUTH_AZURE
TYPE = EXTERNAL_OAUTH
ENABLED = TRUE
EXTERNAL_OAUTH_TYPE = AZURE
EXTERNAL_OAUTH_ISSUER = '<Issuer URL from Identity Provider>'
EXTERNAL_OAUTH_JWS_KEYS_URL = '<Keys Endpoint from Identity Provider>'
EXTERNAL_OAUTH_AUDIENCE_LIST = ('<Application ID URI of Snowflake Resource>')
EXTERNAL_OAUTH_TOKEN_USER_MAPPING_CLAIM = 'sub'
EXTERNAL_OAUTH_SNOWFLAKE_USER_MAPPING_ATTRIBUTE = 'login_name';See Snowflake External OAuth Overview for details on other providers like Okta or custom configurations.
Create the Snowflake service user
A critical step in the Client Credentials flow is mapping the token to a Snowflake user. Since there is no interactive user, the token contains a Subject (sub) claim (often the Object ID of the Client in Azure/Entra ID).
You must create a Snowflake user where the LOGIN_NAME matches this unique identifier exactly.
-- The LOGIN_NAME must match the 'sub' or 'oid' claim from the decoded access token
CREATE USER SNOWSQL_OAUTH_USER
LOGIN_NAME = '3d63d2ef-abb5-xxxx-xxxx-c72c0652895d'
DISPLAY_NAME = 'Service Account User';
-- Grant the role specified in the token scope
GRANT ROLE ANALYST TO USER SNOWSQL_OAUTH_USER;Configure Posit Connect
The Posit Connect administrator creates an OAuth integration in Connect.
Important: Do not use the “Snowflake” template in Connect for this flow. Instead, create an integration for the Identity Provider that is issuing the tokens.
- Go to System > Integrations.
- Create a new Azure (or Custom) integration.
- Select the Service Account authentication flow (Client Credentials).
- Enter the
Client IDandClient Secretgenerated for the OAuth Client in step 1. - Ensure the scopes include the Snowflake Resource identifier (e.g.,
api://<snowflake_app_id>/.default).
Once configured, content on Connect will authenticate as the mapped Snowflake user (e.g., SNOWSQL_OAUTH_USER) without requiring manual sign-in.
Next steps
Once the integration is configured, publishers can use it in their content. See the following cookbook recipes for examples: