OAuth Integrations
This section describes how to use OAuth integrations in Posit Connect. OAuth integrations allow content publishers to securely access short-lived OAuth access tokens with limited permissions. Using an OAuth access token in published content is more secure than embedding long-lived credentials (like Personal Access Tokens) when accessing protected resources in an external system, like Azure, Databricks, or Snowflake.
Access tokens are issued to Connect by an external system and are used to access protected resources. Access controls for the protected resource are defined by the external system, not by Connect. This allows administrators of the external system to create fine-grained access controls in a single source and delegate those permissions to Connect. Delegated permissions coming from a single source of truth are less likely to fall out-of-sync than coordinating permission rules across many published apps.
OAuth integration types
Authentication types
Viewer
By default, all OAuth integrations in Connect use the Viewer authentication type, which implements the OAuth 2.0 Authorization Code Grant Type. Viewer OAuth integrations provide content publishers with an OAuth access token which represents the identity of the content viewer. This allows content to access protected resources on behalf of the viewer, providing a personalized experience when interacting with deployed content on Connect.
When deployed content is configured to use a Viewer OAuth integration, the content viewer is redirected to a consent screen after visiting the content for the first time. The viewer must explicitly grant Connect permission to access the protected resources on their behalf.
Once the viewer consents, they are redirected to the content running in Connect. The content then uses the viewer’s credentials when making requests that require access to protected resources. If multiple Viewer OAuth integrations are associated with the content, the viewer will be redirected to each integration’s consent screen to ensure that there is an active authenticated session for each one.
Assuming the content viewer has granted consent after visiting the content for the first time, the publisher has access to the viewer’s OAuth token. Content publishers who use OAuth integrations are responsible for keeping the viewer’s OAuth token secure. Publishers should not attempt to store or cache the OAuth token in any way. Only the access token (short-lived, scoped permissions) is exposed to the publisher.
OAuth refresh tokens are never exposed to the publisher.
Service account
Some OAuth integrations support the Service Account authentication type, which implements the OAuth 2.0 Client Credentials Grant Type. Service Account OAuth integrations provide content publishers with an OAuth access token which represents a service account identity configured in the external system, rather than a specific viewer. This allows content to access protected resources using the service account identity, which will provide the same experience for all users when viewing deployed content on Connect.
Importantly, this service account identity is curated and maintained by Connect, rather than the content item itself. This means that Connect admins have a centralized source-of-truth for sensitive credentials which is auditable. Service account credentials are easily revoked or rotated by Connect admins.
Access control lists
By default, all publishers are able to associate any OAuth integration with their content. This may not be desirable for some integrations, for example, a Service Account OAuth integration grants all publishers and viewers on Connect access to the Service Account’s identity and affiliated permissions. Some external systems may require stricter access control for this identity.
Administrators can restrict publishers’ ability to associate specific integrations with their content via user and group-based access control lists (ACLs). These publisher ACLs are configured per-integration by a Connect administrator. Any users or groups not explicitly included in the ACL will be unable to associate that particular integration with content for which they have publisher permissions.
Be aware that the use of integration ACLs can create situations where a content owner and their collaborators have different sets of permissions. Connect handles this situation with the following behavior on a per-content basis: - All integrations that have been associated with the content will be visible to all viewers with access to the content. Publishers are only able to get additional configuration details about the integration if they are on its ACL. - All publisher collaborators have the ability to remove any association from the content, regardless of ACL restrictions. The publisher will only be allowed to reassociate the integration if they are on its ACL.
See the Integration Management section of the Connect User Guide for additional information on how to use the Integrations tab on the System page to configure ACLs for OAuth integrations.
Supported content types
OAuth integrations which use Viewer authentication only support interactive content. OAuth integrations which use Service Account authentication support interactive and rendered content.
Static content is not supported by OAuth integrations.
| Auth Type | Interactive | Rendered | Static |
|---|---|---|---|
| Viewer | Yes | No | No |
| Service Account | Yes | Yes | No |
Supported access patterns
Public access (No login required) and Share Links are not supported for Viewer integrations. Both content access patterns are supported for Service Account integrations.
| Auth Type | Public Access | Share Links |
|---|---|---|
| Viewer | No | No |
| Service Account | Yes | Yes |
First-class vendor support
Connect provides first-class OAuth integrations against many popular third-party vendors. If a third-party vendor is not natively supported by Connect, the Custom OAuth integration type can be used to communicate with any external system that implements OAuth 2.0.
All OAuth integration types support Viewer authentication. Service Account authentication is conditionally supported by some types of integrations.
| Integration Type | Viewer | Service Account |
|---|---|---|
| AWS | Yes | Yes |
| Azure | Yes | Yes |
| Azure OpenAI | Yes | Yes |
| Azure Databricks | Yes | Yes |
| Custom | Yes | Yes |
| Databricks | Yes | Yes |
| GitHub | Yes (default) | No |
| Google BigQuery | Yes (default) | No |
| Google Drive | Yes (default) | No |
| Google Sheets | Yes (default) | No |
| Google Vertex AI | Yes (default) | No |
| Microsoft Graph | Yes | Yes |
| Palantir Foundry | Yes | No |
| Salesforce | Yes | Yes |
| SharePoint Online | Yes | Yes |
| Snowflake | Yes (default) | Yes (federated) |
Configuring and using an OAuth integration
Personas
To configure and use an OAuth integration in Connect, the following personas are required:
- OAuth application administrator - creates an OAuth application in an external system.
- Connect administrator - creates an OAuth integration in Connect.
- Connect publisher - authors the content which accesses protected resources. For more information on authoring content that accesses protected resources, see the OAuth Integrations section of the User Guide.
- Connect viewer - views the deployed content on Connect.
Persona responsibilities
The following section describes the responsibilities of each persona needed to configure and use an OAuth integration in Connect. The role of each persona is ordered chronologically, but some personas may overlap as they communicate information back-and-forth.
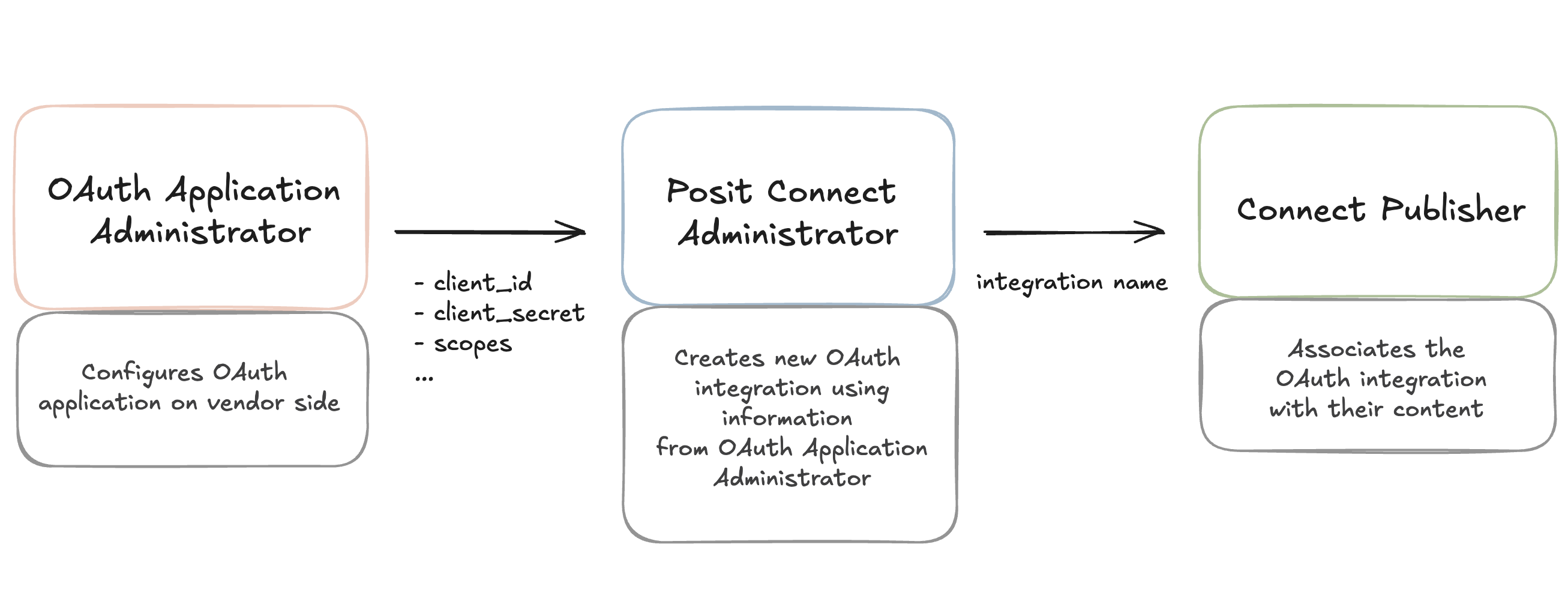
Below is a diagram to help visualize the handoffs that must happen between the OAuth application administrator, Connect administrator, and Connect publisher in the process of configuring an OAuth integration.
OAuth application administrator
The OAuth application administrator in the external system registers a new OAuth application that can issue OAuth tokens to Connect.
If the Connect OAuth integration uses Viewer authentication, the OAuth application administrator configures the application with the following redirect URL (sometimes referred to as a callback URL): https://connect.example.org/__oauth__/integrations/callback, replacing connect.example.org with the address of the Connect server.
For OAuth application administrators who prefer to use the same OAuth application for both Posit Connect and Posit Workbench, simply register the Workbench redirect URL (https://workbench.example.org/oauth_redirect_callback) in addition to the Connect redirect URL.
Once the OAuth application is registered, the OAuth administrator provides the following information to the Connect administrator:
client_id(required) - The client ID identifies the OAuth application.client_secret(optional) - Required for Confidential OAuth applications and Service Account OAuth integrations. Sometimes referred to as an app password.scopes(optional) - A list of allowed OAuth scopes (permissions) that can be requested.
There are additional fields that are required depending on the type of OAuth integration being created. See the associated documentation for each type of integration for details on how to register a new OAuth application.
Connect administrator
The Connect administrator can use either the Connect UI or the Connect Server API to create OAuth integrations.
For details on how to configure new OAuth integrations in Connect, see the associated documentation for each type of integration. The following types of OAuth integrations are supported:
- AWS
- Azure
- Azure OpenAI
- Azure Databricks
- Databricks
- GitHub
- Google BigQuery
- Google Drive
- Google Sheets
- Google Vertex AI
- Microsoft Graph
- Palantir Foundry
- Salesforce
- SharePoint Online
- Snowflake
- Custom
See the Integration Management section of the Connect User Guide for additional information on how to use the Integrations tab to edit, delete, and test integrations.
Connect publisher
The Connect publisher associates OAuth integrations with their content using one of the following three methods. For more information about authoring content that uses OAuth integrations, see the OAuth Integrations section of the User Guide.
Connect Server API
The example below uses curl and the Connect Server API to associate integrations with an existing piece of deployed content in Connect.
Replace connect.example.org with the address of the Connect server.
Terminal
curl -H "Authorization: Key ${CONNECT_API_KEY}" \
-XPUT https://connect.example.org/__api__/v1/content/<content-guid>/oauth/integrations/associations \
--data '[
{"oauth_integration_guid": "<oauth-integration-guid-1>"},
{"oauth_integration_guid": "<oauth-integration-guid-2>"},
...
]'Connect UI
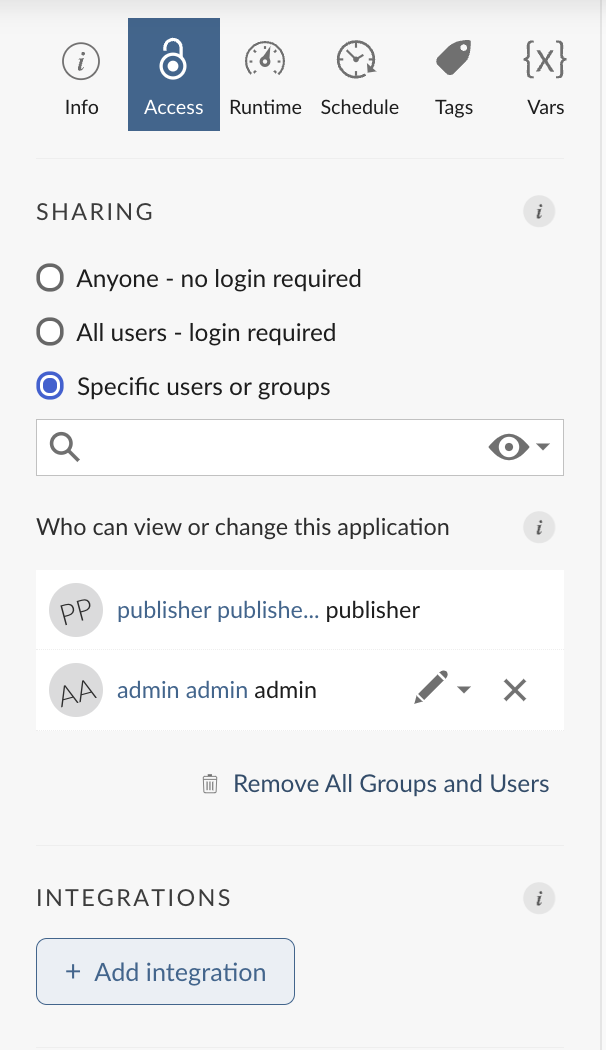
Alternatively, the Connect publisher can associate OAuth integrations with individual pieces of content using the Connect UI following these steps: Settings > Access > Integrations > Select integrations.
Clicking Select integrations opens a modal that allows the Connect publisher to select one or more OAuth integrations.
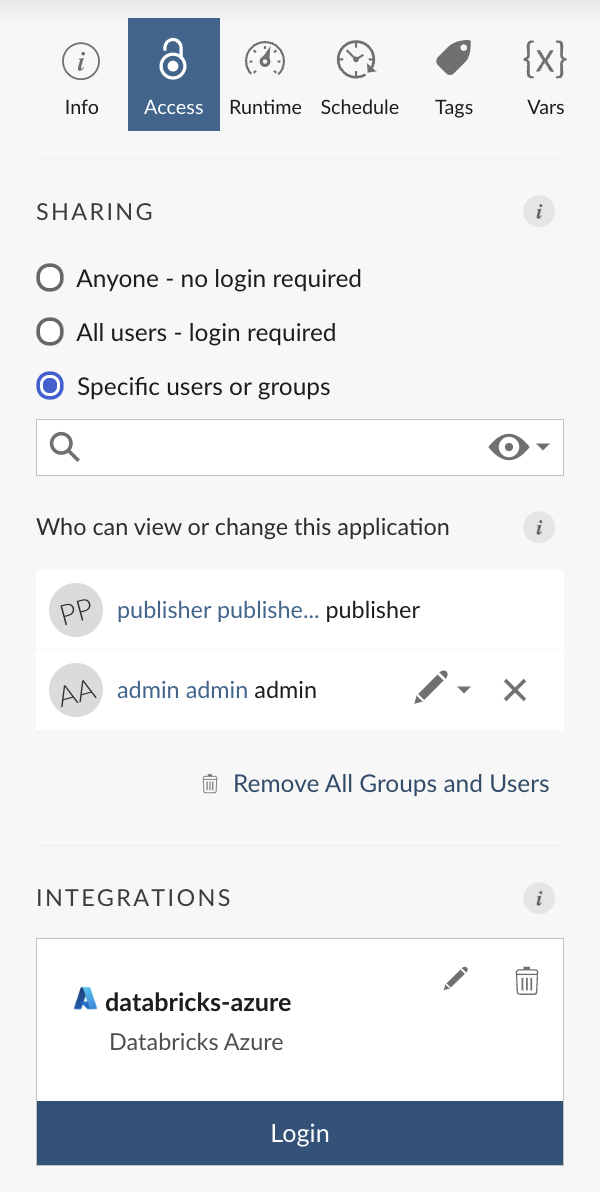
After a Connect Publisher selects integrations and saves, a panel containing information about the integrations appears below the Select integrations button. If an integration uses the Viewer authentication type, a login button is also provided.
Integration requests
OAuth integrations can also be automatically associated with content via integration requests defined in the manifest.json file. For more information about using this feature visit the Manifest section of the Connect User Guide.
The Publisher VS Code extension has an “Integration Requests” pane that can be used to specify OAuth integration requests. This allows you to automatically associate integration requirements with your content without having to directly interact with the manifest.json file.
Connect viewer
If an OAuth integration uses the Viewer authentication type, Connect users who have the Viewer permission on the content item receive a personalized view when they visit the deployed application.
If an OAuth integration uses the Service Account authentication type, the content will execute for all users who have the Viewer permission using the OAuth credentials of the service account identity. If multiple Service Account integrations are used, the content will have access to credentials for each service account. Content will execute identically for each viewer.