Management
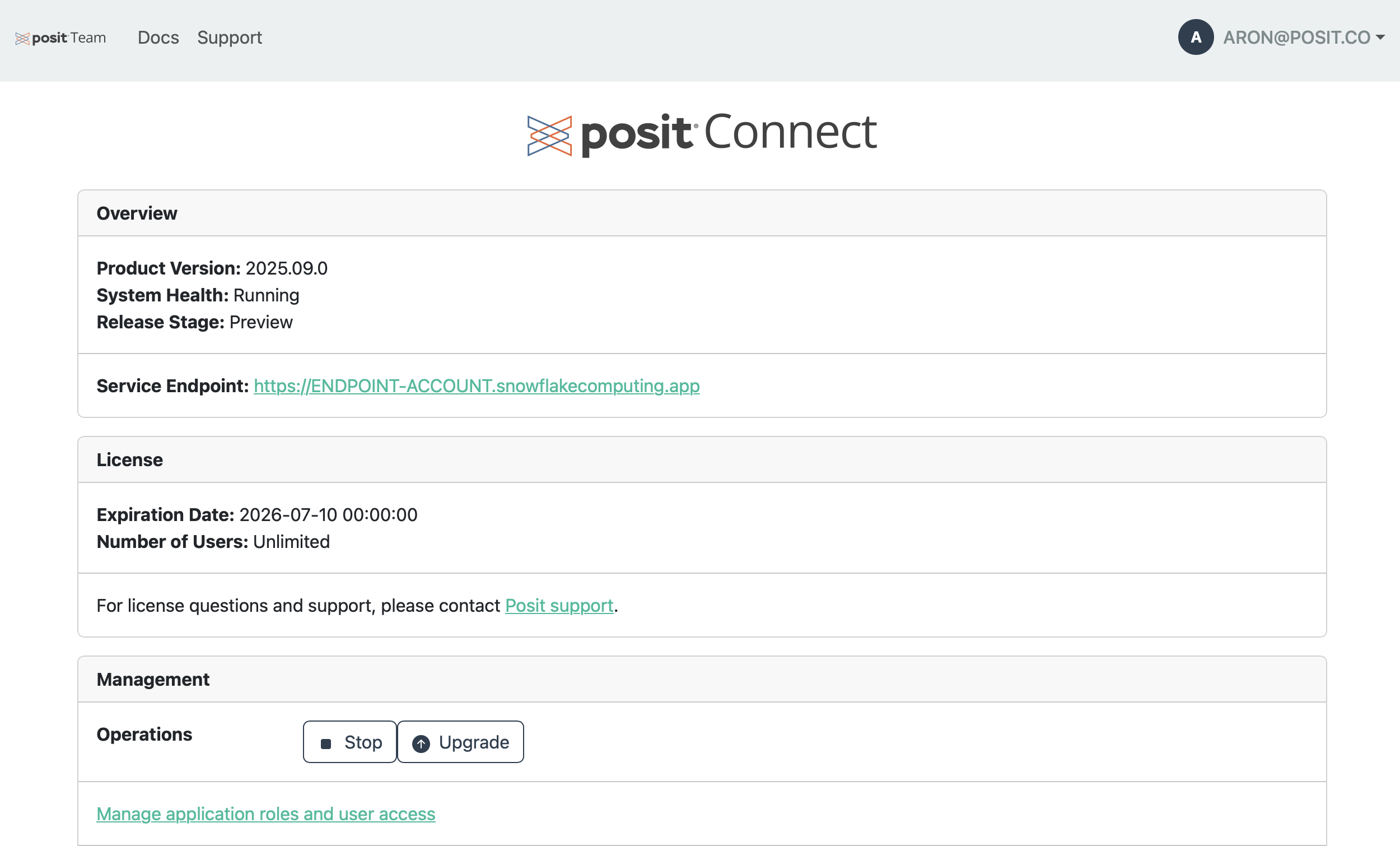
Posit Team includes a Posit Connect management page for an administrator to perform post-installation operations.
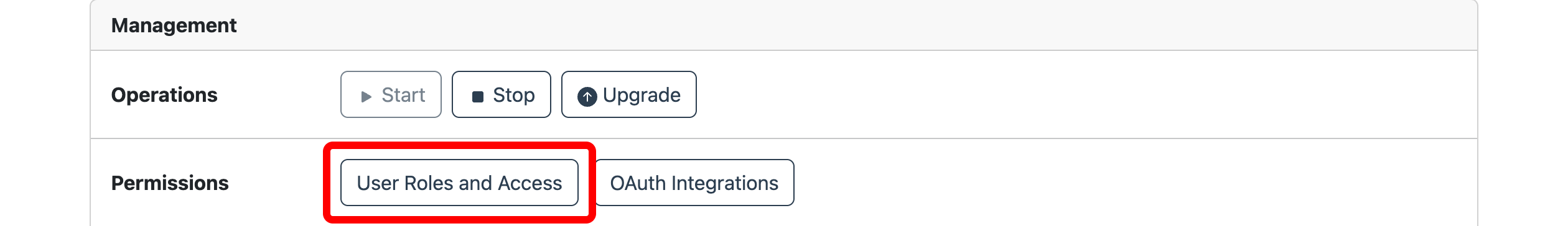
To manage Connect, click the menu icon (vertical dots) on the Connect card and click Manage.
Stop and start
The Connect service can be managed in several ways:
- Manual stop and start.
- Programmatic stop and start.
A suspended Connect service automatically resumes when visited by a user.
If there are times when Connect is not used, such as on weekends and holidays, suspending the service can help reduce your Snowflake compute costs.
Some features of Connect, such as scheduled jobs, do not run while the service is suspended.
You can manually stop and start the Connect service from the Manage page.
You can start and stop the Connect service using SQL commands.
-- Start Connect
SELECT POSIT_TEAM.app.START_SERVICE('connect');
-- Stop Connect
SELECT POSIT_TEAM.app.STOP_SERVICE('connect');Schedule the start and stop of Connect by running these SQL commands with Snowflake tasks.
-- Create a task to stop Connect at 6 PM daily.
CREATE OR REPLACE TASK task_connect_stop
SCHEDULE = 'USING CRON 0 18 * * * America/New_York'
AS
SELECT POSIT_TEAM.app.STOP_SERVICE('connect');
-- Enable the stop task.
ALTER TASK task_connect_stop RESUME;
-- Create a task to start Connect at 8 AM daily
CREATE OR REPLACE TASK task_connect_start
SCHEDULE = 'USING CRON 0 8 * * * America/New_York'
AS
SELECT POSIT_TEAM.app.START_SERVICE('connect');
-- Enable the start task.
ALTER TASK task_connect_start RESUME;Upgrade
Posit frequently upgrades the Posit Team Native App and its associated version of Connect. When the Posit Team Native App is updated, Posit Team automatically upgrades Connect.
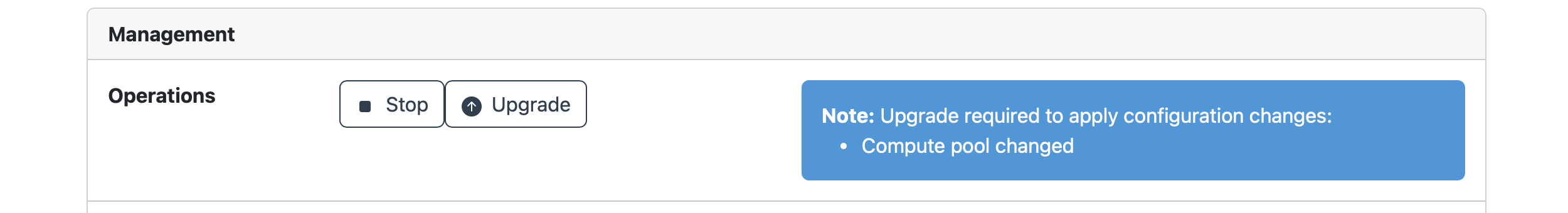
Some configuration changes require a service upgrade before they take effect. For example, you need a service upgrade after modifying the target compute pool or uploading a new license. The management page indicates when configuration changes require an upgrade. Click the Upgrade button to upgrade Connect.
Change configuration
In the management page you can change the license, resize the compute pool, update users roles and access, and update the OAuth integration. If the compute pool, OAuth integration or license have changed, a service upgrade is required. Follow the upgrade section instructions.
Resize compute pool
The Manage page lets you change the compute pool used to run Connect. Choose a compute pool size appropriate to your workload requirements.
Use the upgrade instructions to apply a compute pool change and restart Connect.
Update OAuth credentials
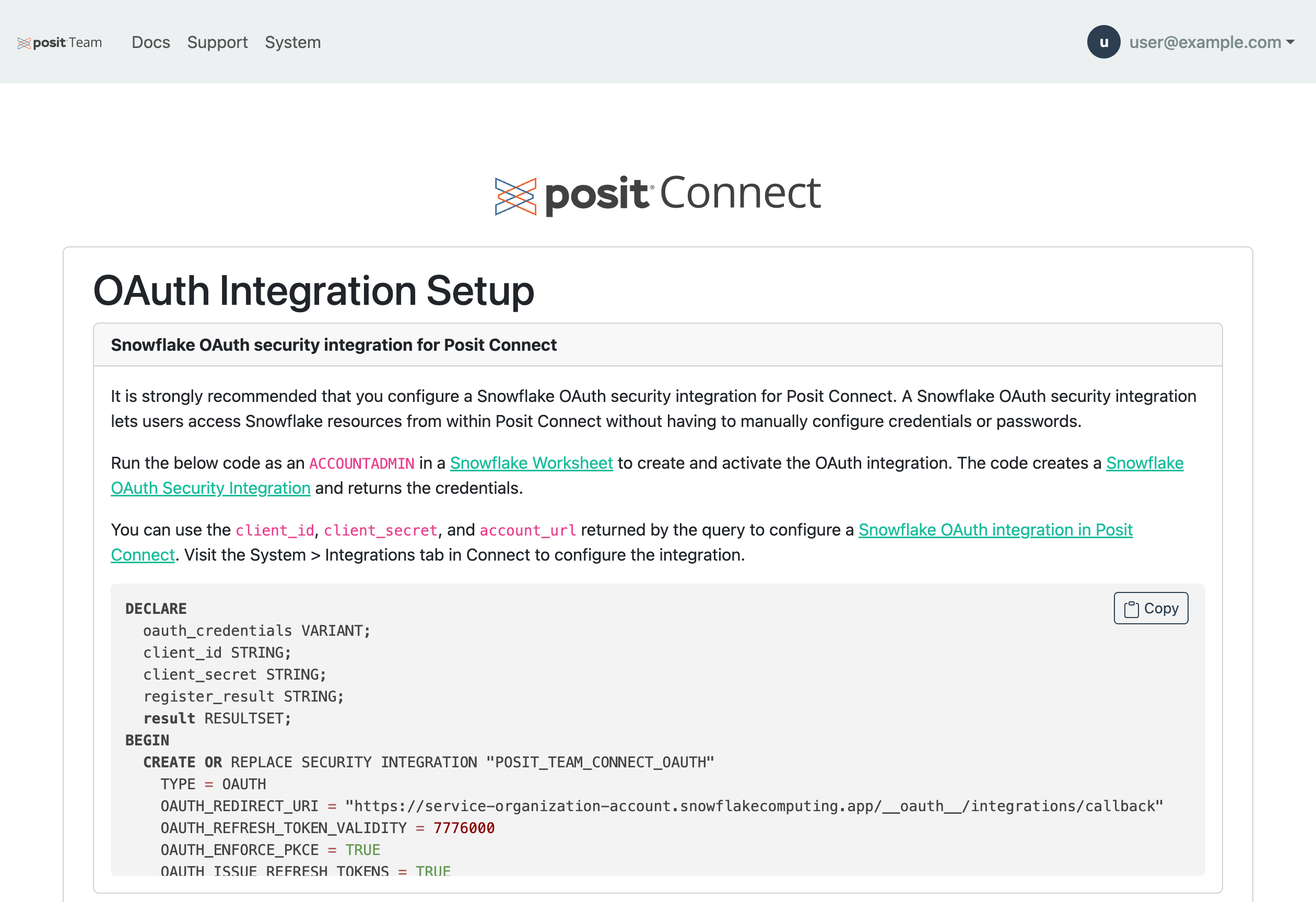
You can modify the Connect Snowflake OAuth integration after its initial setup.
To update the integration:
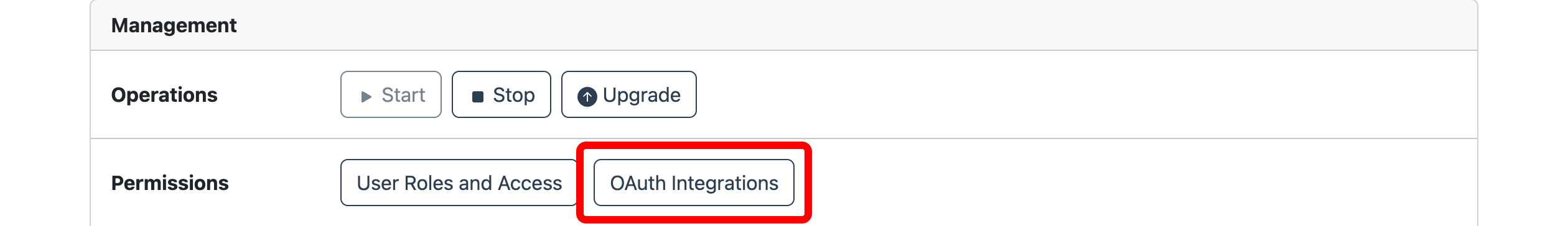
Open the Manage page and click on the OAuth Integrations button.
Copy the generated SQL code and run it in a Snowflake Worksheet as an ACCOUNTADMIN to recreate the integration.
Save the client_id, client_secret, and account_url returned by the query.
Visit the System > Integrations tab in Connect to update the integration or create a new one.
Use the values copied above to configure the Snowflake OAuth integration in Posit Connect.
Backup and restore
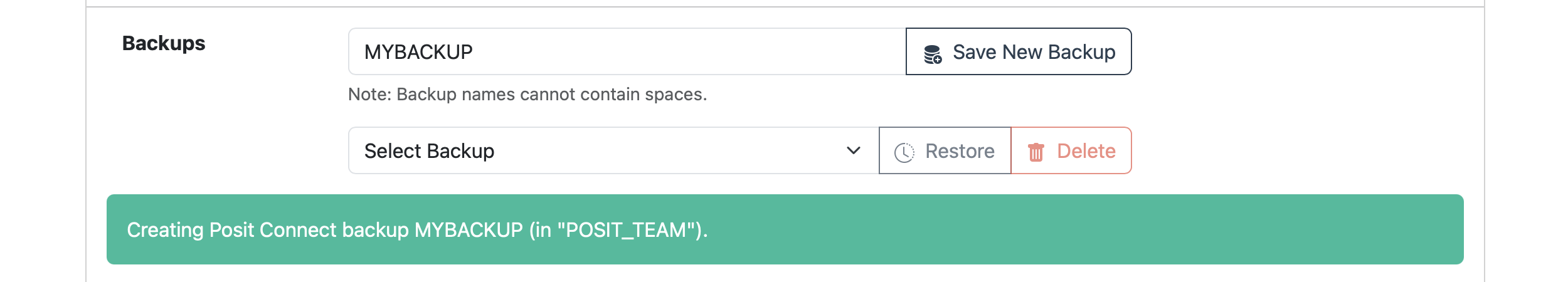
Posit Team supports easily creating Connect backups. Simply specify a backup name or leave it blank for a randomly assigned name and click Save New Backup.
Next, wait several minutes for the backup to be created.
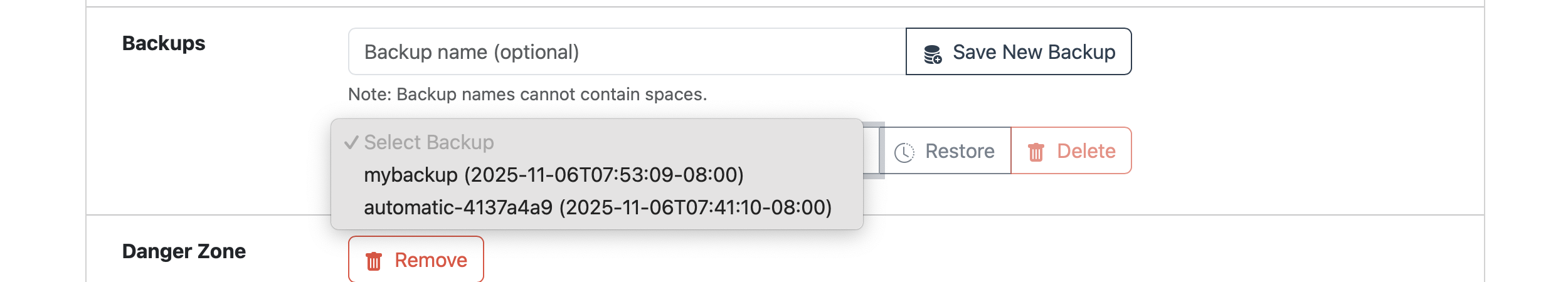
Restoring from a backup takes about 10 minutes. You can delete backups that are no longer needed.
Logs
You can view logs of the Connect installation.
User access
In order for Snowflake users to access Connect, you must grant access to their user roles. We recommend you grant the application role POSIT_TEAM_USER to most users.
Snowsight UI
GRANT APPLICATION ROLE POSIT_TEAM.POSIT_TEAM_USER TO ROLE YOUR_USER_ROLE;To restrict user access to Connect only give the application role POSIT_CONNECT_PUBLISHER to those users. See Managing Application Roles to learn more.
Snowsight UI
GRANT APPLICATION ROLE POSIT_TEAM.POSIT_CONNECT_PUBLISHER TO ROLE YOUR_USER_ROLE;Connect groups
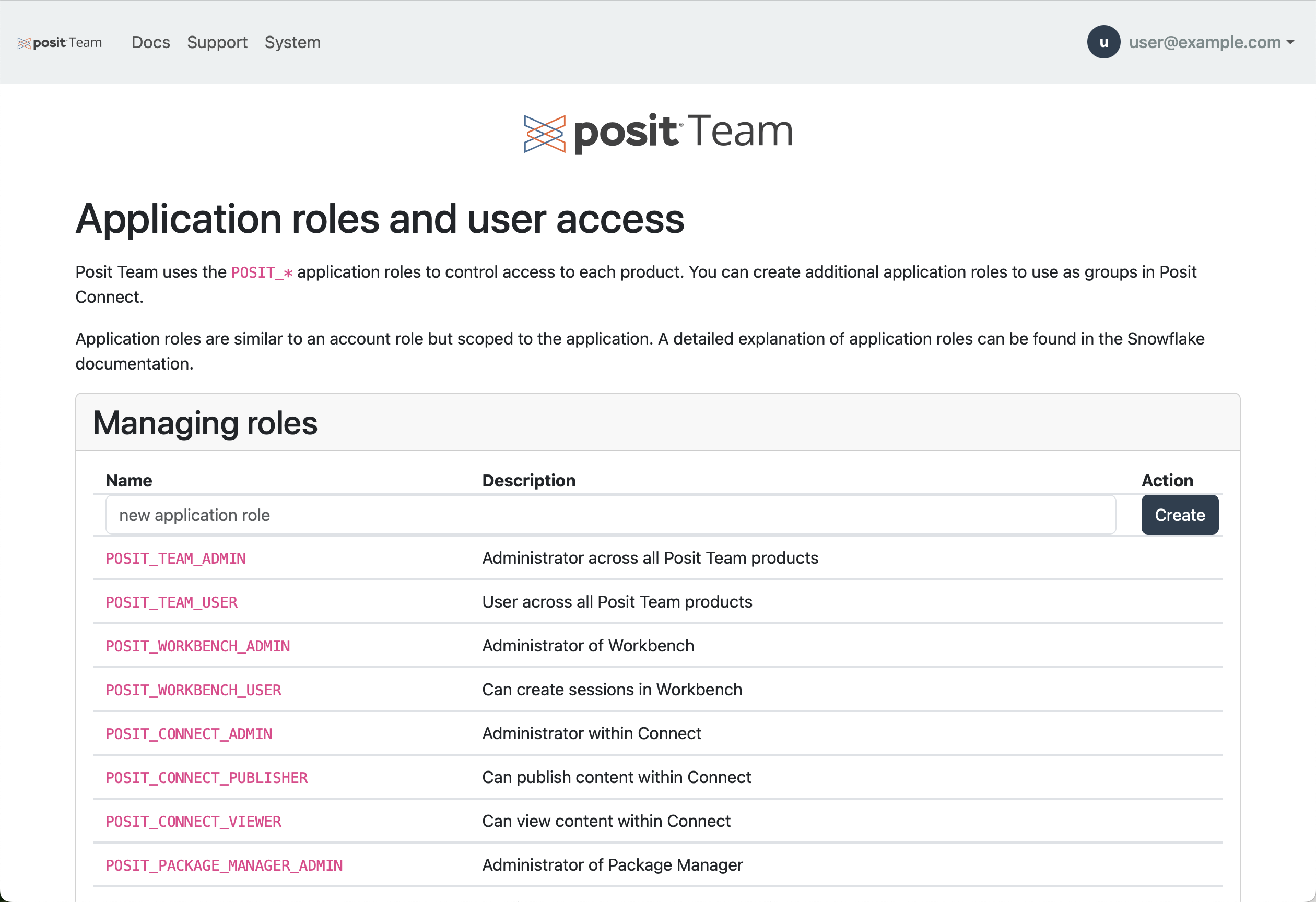
You can create additional application roles to use as groups in Posit Connect. Publishers and Collaborators can use “groups” to associate multiple users to content as viewers or collaborators. This can often provide an easier alternative to maintaining a discrete list of users associated with each instance of published content. Note that POSIT_* is a restricted prefix for additional application roles.
To add a new application role click on User Roles and Access in the Management page for Connect.
Add your custom application role to the Managing roles table and press Create.
Change the egress
To ensure full product functionality, key endpoints must be accessible, such as those for Snowflake OAuth and the Online Certificate Status Protocol (OCSP). For more information, see the security egress traffic documentation.
Editing the default egress policy requires the ACCOUNTADMIN role. You can modify the default egress policy for Connect by:
- Using the Snowsight UI (recommended) or
- Writing your own SQL
To edit network rules via Snowsight UI:
Visit Governance & security -> Network policies -> Network Rules.
Edit the given network rule named POSIT_TEAM_APP_DATA.DATA.CONNECT_PUBLIC_EGRESS and remember to include the required endpoints detailed in the security egress documentation.
To edit network rules via SQL:
Modify the existing network rule POSIT_TEAM_APP_DATA.DATA.CONNECT_PUBLIC_EGRESS.
Snowsight UI
DESCRIBE NETWORK RULE posit_team_app_data.data.connect_public_egress;
--- include custom <host>:<port>
--- host names are allowed
--- this example policy allows all ips on port 80 and 443
ALTER NETWORK RULE posit_team_app_data.data.allow_all_rule SET VALUE_LIST('0.0.0.0:80', '0.0.0.0:443');Modify the egress rules only after a successful installation, and only change one rule at a time, allowing two to three minutes for each rule to take effect.
Troubleshooting and support
Visit the troubleshooting page for known issues and troubleshooting steps. If none of the troubleshooting steps help, please submit a request through the Posit support form or click on the Support button in the navigation header.